“Data is the pollution problem of the information age, and protecting privacy is the environmental challenge.” ~ Bruce Schneier
In an era defined by technological quantum leaps, the ubiquity of data, and the interconnectedness of devices, the cybersecurity industry positions itself as the digital bulwark protecting businesses, governments, and individuals from an ever-evolving landscape of threats, some of them existential. As our lives become increasingly intertwined with digital platforms, the demand for robust cybersecurity solutions has skyrocketed, propelling this sector into a realm of practically unrivaled significance.
Within the labyrinth of code libraries, server farms, networks, and firewalls lie not only vital security measures but also lucrative investment opportunities that beckon astute investors. In this Signal From Noise, we explore the core trends shaping the cybersecurity industry, look at some of the key players leading and exploiting these trends, and unveil actionable investment ideas that promise to harness the potential of this booming sector.
The Cybersecurity Landscape: Navigating Complexity Amid Chaos
As technologies advance in their capability and complexity, so do the threats that seek to exploit them for profit or in service of an ideology. Whether preempting sophisticated breaches or mitigating crippling attacks, the cybersecurity industry seeks to be an agile and formidable force commanding a high-stakes battleground. To gain an investor’s edge when approaching cybersecurity stocks, one needs to fully grasp the shifting dynamics of the industry’s landscape.
- The rise of nation-state attacks. Governments and state-sponsored entities are increasingly deploying cyber-warfare tactics, targeting critical infrastructure and sensitive data. Tracking companies that specialize in fending off threats from nation states is a solid medium-term strategy, as governments worldwide prioritize the bolstering of their digital defenses.
- AI and machine learning. The cybersecurity industry has harnessed the power of artificial intelligence and machine learning to identify patterns, predict attacks, and muster responses faster than ever before. Investment in AI-driven cybersecurity solutions could yield significant returns, as automation – in the sense of ever-increasing delegation of low-level, high-volume decision-making to AI – becomes a cornerstone of defense mechanisms.
- Zero-trust architecture. Traditional perimeter-based security models are giving way to zero-trust architecture, which treats every user and device as potentially compromised. Companies offering zero-trust solutions are likely to experience increased demand, resulting in investment opportunities.
Geography, Infrastructure, Regulation, Opportunities
According to The Business Research Company’s Cybersecurity Global Market Report 2023, the global cybersecurity market will grow to $223.7 billion in 2023 (from $201.3 billion the year before) at a CAGR of 10.9%. By 2027, it is expected to grow to $338.8 billion, maintaining roughly the same growth rate.
Asia, primarily driven by rapid digital transformation and integration, is due to see significant growth. India’s expansive digital infrastructure projects underscore this trend, and so does China’s commitment to becoming a global tech superpower – at least in the short term.
Asia Pacific was the largest region in the cybersecurity market, accounting for 38.7% of the total market share in 2022. Looking ahead, South America and the Middle East are forecast to be the fastest-growing cybersecurity markets.
Regulatory frameworks are evolving to address escalating cybersecurity concerns. For investors, understanding these regulations can unearth true opportunities.
GDPR and Data Protection. Recent surges in cyber-attacks, especially ransomware incidents, in Europe and beyond, as well as the rising cost of data breaches, have brought home in the starkest way possible the indispensable nature of robust cybersecurity frameworks. The General Data Protection Regulation (GDPR) imposes hefty fines in cases of compromised data. This has reshaped how businesses handle personal data; it’s also pushed companies to make greater investments in cybersecurity.
Critical Infrastructure Protection. Governments worldwide are enacting regulations to safeguard critical infrastructure from cyber threats. It makes sense to keep an eye out for companies specializing in cybersecurity solutions made specifically for sectors such as energy, transportation, and healthcare.
U.S. Government Support. Through the Infrastructure Investment and Jobs Act (IIJA) of 2021, Congress established the State and Local Cybersecurity Improvement Act and, through the State and Local Cybersecurity Grant Program, allocated $1 billion to address cybersecurity risks and threats to their information systems at the state and local levels. Another $600 million was set aside in cyber-related support for the power, water, and transportation infrastructures.
In early March of this year, the White House published a National Cybersecurity Strategy, laying out a plan to use executive orders and memoranda to improve cybersecurity for critical infrastructure control systems, move the U.S. government toward zero-trust cybersecurity principles, and promote U.S. leadership in quantum computing while mitigating risks to vulnerable cryptographic systems.
Investment Contours
The ramping up in cybersecurity infrastructure investment presents potential opportunities for companies in five of the seven primary industry subcategories outlined below. There is considerable overlap, with certain companies taking the lead in multiple subcategories.
Cloud Security
Cloud adoption is on the rise, with enterprise cloud migrations becoming business-critical initiatives. Evolving security capabilities mean that enterprises can retain control over their security posture, data protection programs, and application integrity. The leading players are architecting security solutions for the cloud, combining control and integrity with scalability and agility.
Key participants in this space include:
- Palo Alto Networks (PANW -1.32% )
- Zscaler (ZS -5.47% )
- Check Point Software Technologies (CHKP -0.01% )
Security of Things
IoT device connectivity can unlock new business value, but as IT networks and operational technology (OT) networks have converge, the attack surface is now larger, and adversaries can threaten health and safety, not just steal data.
Ransomware and 5G are changing the OT threat landscape, with ramifications on the supply chain and physical world, including personal safety. New models and mindsets are needed to mitigate these new threats.
Key participants in this space include:
- CrowdStrike (CRWD -7.95% )
Perimeterless World
The enterprise perimeter is largely a beast of the past, nearly extinct. The shift to remote work post-COVID and the rise of SaaS – and the attendant greater reliance on the cloud, as well as the increased risk of insider threats – accelerate its demise. This makes identity and zero-trust architectures increasingly important in governing access management, to support new ways of doing business that drive growth, productivity, and competitive advantage.
Key participants in this space include:
- Zscaler (ZS -5.47% )
- Okta (OKTA -9.61% )
Privacy & Digital Trust
Globalization and expanding digital commerce are on a collision course with emerging privacy regulations and consumer preferences, with resulting data breaches as well as large fines for non-compliance. The design of business processes and systems architecture needs to accommodate new privacy and zero trust-driven strategies.
Know your data (KYD), from knowing what you have, storing only what you need, and leveraging technologies that make it possible to do business without sharing data will become critical.
Resilience & Recovery
Digital infrastructure has become business-critical, which means that recovery from cyberattacks is now core to risk mitigation and business continuity. Operational resiliency, i.e. rapid recovery and reconstitution of assets and capabilities, must be part of any sound security strategy.
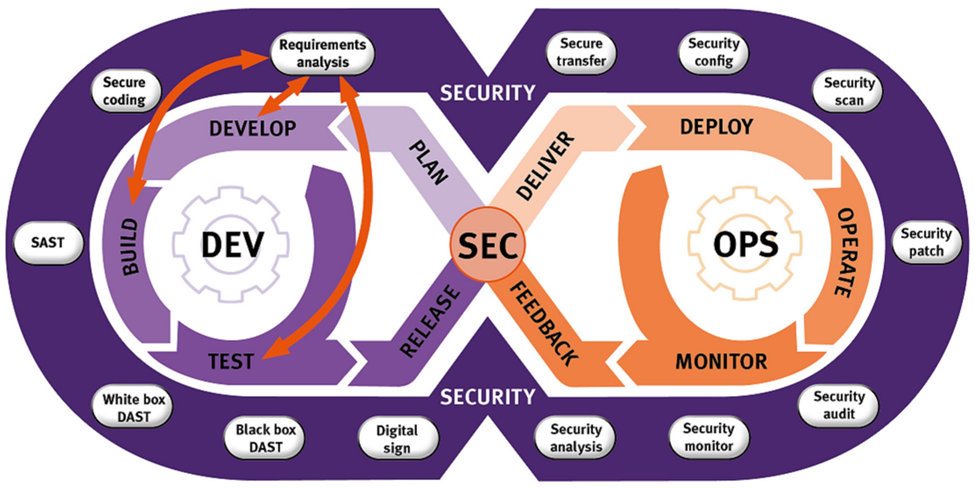
Shift-Left
Software development and management is becoming more agile than ever. Security cannot be an afterthought, but must be baked in, or ‘shifted-left’ to the developers, who will embed security considerations from the start in a DevSecOps model, with security-by-design and code-to-production being the new business standards. In other words, security professionals should understand coding, and developers need to code with security in mind.
Key participants in this space include:
- Palo Alto Networks (PANW -1.32% )
Smarter Security
As organizations face unprecedented security complexity, response capacity is stretched to its limits —an expanding enterprise network, unintegrated products, a cyber-talent shortage, and hackers with increasingly sophisticated capabilities. Smarter security solutions are leveraging automation, data, and AI to handle routine tasks, leaving humans with the bandwidth to focus on managing exceptions.
Key participants in this space include:
- Palo Alto (PANW -1.32% )
- Splunk (SPLK)
- Datadog (DDOG -4.10% )
Riding the Investment Wave
Historically recession-resistant – and currently the fastest-growing, highest-priority subsector of the software sector – cybersecurity is seen by the c-suite at large companies as non-negotiable in terms of spending.
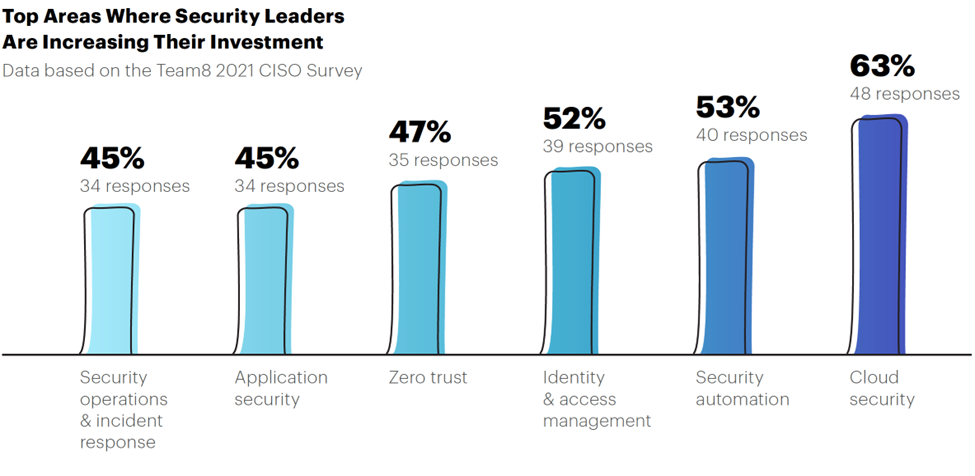
Indeed, in our view, security is the fastest-growing top-priority concern for CIOs, with the hiring of a CISO (Chief Information Security Officer) becoming standard practice at large companies across the economy. Cyber also tends to be a non-discretionary budget item, which creates a large market opportunity – and, by extension, an attractive investment opportunity – specifically via these companies, all paragons of growth and profitability, as well as long-term outperformers.
- Cloudflare (NET -8.05% ) – A leader in delivering cloud cybersecurity and DDoS mitigation.
- CrowdStrike (CRWD -7.95% ) – Specialists in endpoint security using cloud-native architecture.
- Palo Alto Networks (PANW -1.32% ) – Known for their next-generation firewalls and cloud-security solutions.
- ZScaler (ZS -5.47% ) – Champions of Zero Trust Network Access solutions.
- Okta, Inc. (OKTA -9.61% ) – An identity and access-management leader that provides cloud software that provides user-authentication management, including identity controls for applications.
- Check Point Software (CHKP -0.01% ) – Innovators in firewall protection and VPN security.
- Splunk (SPLK) – Analytics-driven security with real-time threat intelligence.
As does any industry, the cybersecurity domain faces obstacles. Rapid technological advancement implies that today’s security solutions might become obsolete tomorrow. The industry also grapples with a shortage of skilled cybersecurity professionals.
To mitigate these challenges, firms are investing in AI and machine learning for proactive threat detection, exploring quantum cryptography to address future computing challenges, adopting zero-trust architectures to minimize internal vulnerabilities, and expanding cyber threat intelligence to provide real-time, global threat feeds.
Two high-tech titans enabling these companies’ technologies include IBM (IBM 0.34% ), which leads in quantum computing and its implications for security, as well as NVIDIA (NVDA 1.03% ), which is aggressively expanding into AI-driven cybersecurity solutions.
A Secure Future with Lucrative Prospects
The relentless nature of the cybersecurity industry’s expected growth trajectory paints a picture of unending opportunities. From defending against nation-state attacks to securing the IoT landscape, the sector is abuzz with innovative solutions and investment potential. Discerning the true value signal amid the noise of possibilities requires careful consideration, research, and a deep understanding of the industry’s dynamics.
The industry has reason to be optimistic in the face of certain tailwinds, but it is also subject to uncertainty and growth limitations. On the one hand, cybersecurity is coming into the mainstream, with the CISO finally being viewed as a key decision-maker and profit enabler, not just risk-mitigation and cost-avoidance specialist. Due to the pandemic, organizations are now on high alert for phishing and other forms of attacks and scams that can lead to data breaches.
At the same time, as the industry matures, cybersecurity needs more standardization and compatibility, e.g. more intuitive application interfaces optimized for the behavior of security professionals, more security-by-design and greater collaboration with developers, more automation, consolidation, and less involvement of trust and the human factor. Ultimately, the companies that rise to the moment with workable, cost-effective solutions to these challenges are the ones to watch.
As usual, Signal From Noise should serve as a starting point for further research before making an investment, rather than as a source of stock recommendations. Although the names mentioned above each have the potential to benefit from increased government investment in cybersecurity infrastructure globally, this alone should not be the basis of a decision to invest.
We encourage you to explore our full Signal From Noise library, which includes deep dives on the the world of Big Data and opportunities arising from the global transition to electric vehicles. You’ll also find a recent discussion on private-sector intelligence and the aging U.S. power grid.






